One of the original building blocks of AWS, Amazon S3 buckets continue to be the core storage facility for cloud-based organizations. The original goal was to ensure that organizations could use public buckets and objects easily, providing tools to limit public access. Because S3 has occasionally been a newsworthy security topic, AWS makes changes to shore them up. In April 2023, several important Amazon S3 security changes are coming, so if you use S3 buckets, you’ll want to know what to expect. AWS will roll out the changes all AWS Regions within a few weeks.
How AWS Controls Access to Data
If you have ever created an S3 bucket, you have answered a series of questions that set the original configuration. For example, you set the name and region for a new bucket. Then Amazon asks a series of questions to authorize users for accessing data stored in AWS. Once created, you can manage permissions by creating policies and attaching them. You can use AWS Identity and Access Management (IAM), AWS Organizations, Amazon Cognito, and AWS Resource Access Manager to grant, limit, and monitor access.
Securing New Buckets with S3 Block Public Access
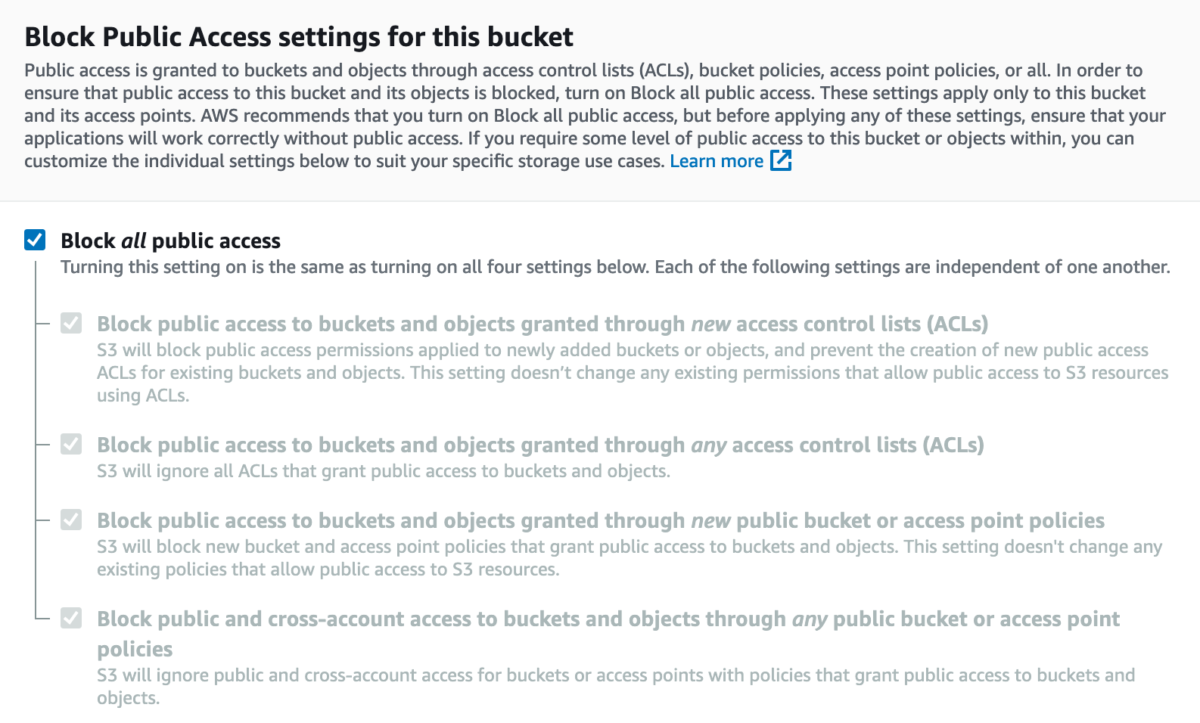
AWS employs a new default setting that automatically enables S3 Block Public Access when you create a new bucket. Block Public Access provides controls across your AWS Account or individual S3 buckets to prevent open public access by default (it’s been a setting for a while, but is the default now). In the new security model, the bucket owner will configure buckets to be public or use access control lists (ACLs).
Amazon S3 Security Changes Are Coming
Note, the default for Block Public Access affects:
- New ACLs
- Any ACLs
- New public bucket or access point policies
- Any public bucket or access point policies
Securing New Buckets by Disabling S3 Access Control Lists
AWS is also changing the default setting for ACLs, which will be disabled on all new S3 buckets. Disabling ACLs is expected to prevent accidental exposure of sensitive data and data breaches. For the past couple of years, ACLs have enabled controlling access to S3 buckets and objects. Their complexity has occasionally led to misconfigurations.
Historically, when another AWS account uploaded an object to your S3 bucket, that account (the object writer) owned the object, had access to it, and could grant other users access to it through ACLs. With the update, ACLs will be automatically disabled – the bucket owner is the object owner no matter who uploads the object.
Overriding the Defaults
Of course, account administrators can override the default settings. In some cases, you may need to update CloudFormation templates other infrastructure configuration tools to configure these settings.
To enable ACLs for a bucket, you can set the ObjectOwnership parameter to ObjectWriter or you can call DeleteBucketOwnershipControls after you create the bucket. Check out Controlling Ownership of Objects and Creating a Bucket.
AWS recommends sticking with the default settings unless there’s a specific need.
For Existing Buckets…
The changes do not impact existing buckets (imagine what it could break!). That said, it’s a great idea to audit your Amazon S3 bucket access to prevent any issues.


Leave A Comment